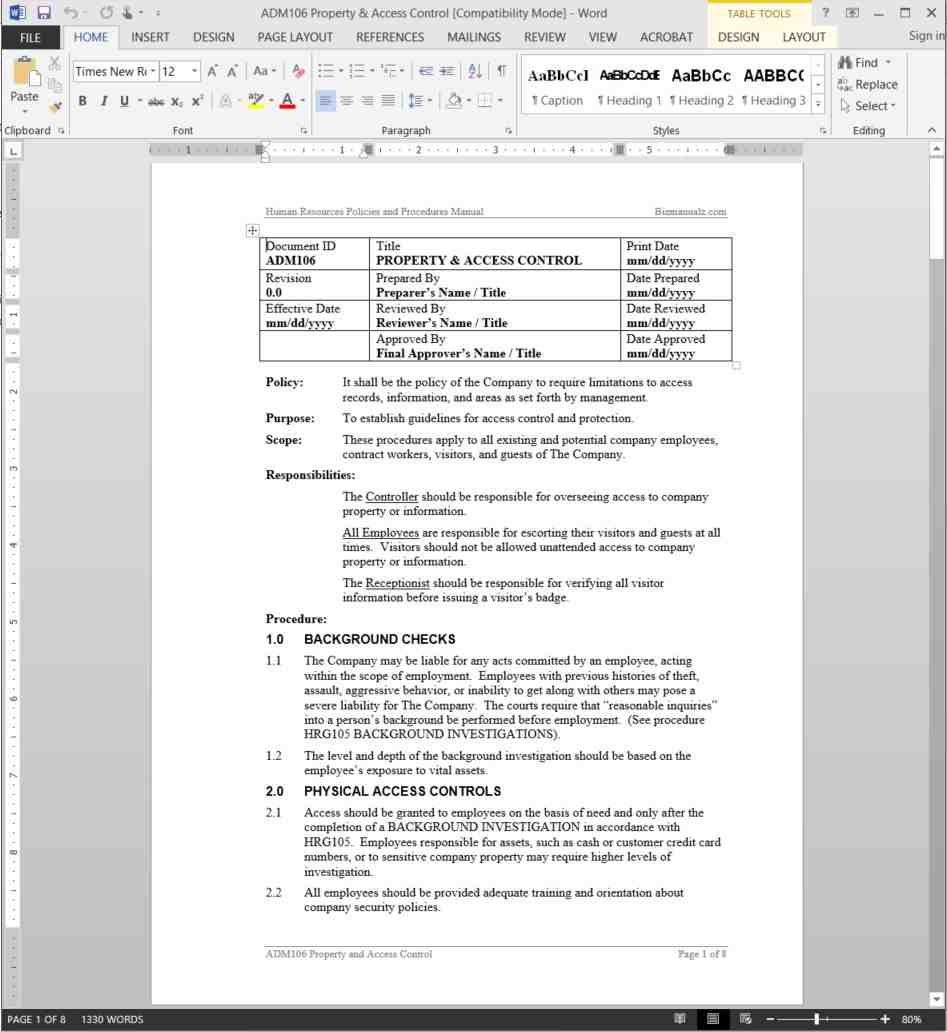
Enforcing Role-Based Access Control with Attribute-Based Cryptography for Environments with Multi-Level Security Requirements | Semantic Scholar
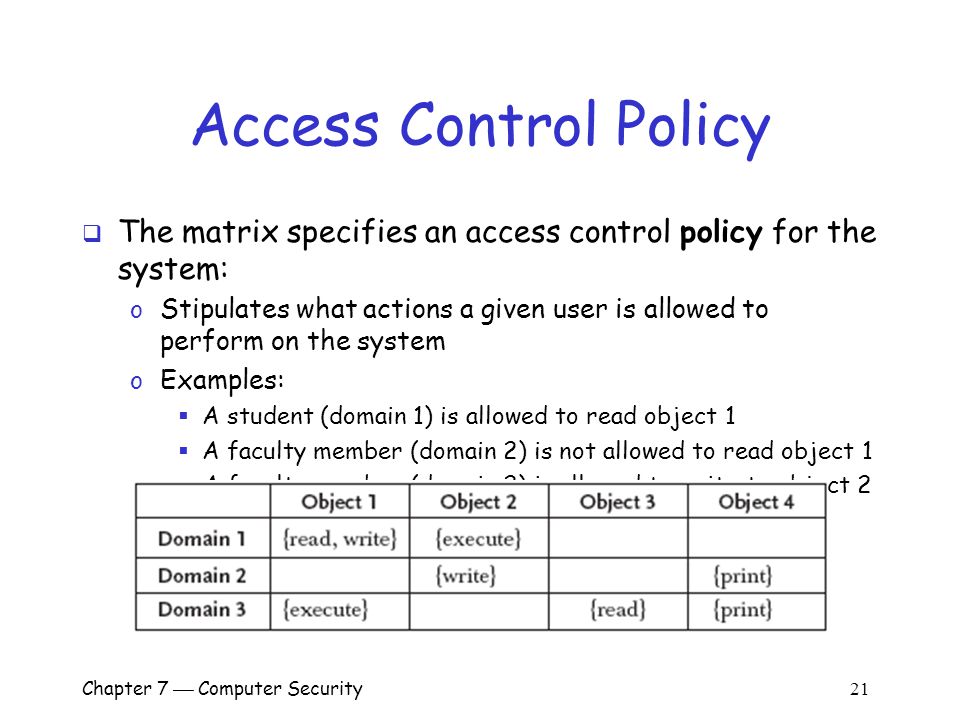
Chapter 7 Computer Security 1 Overview Important components of computer security: o User authentication – determine the identity of an individual accessing. - ppt download
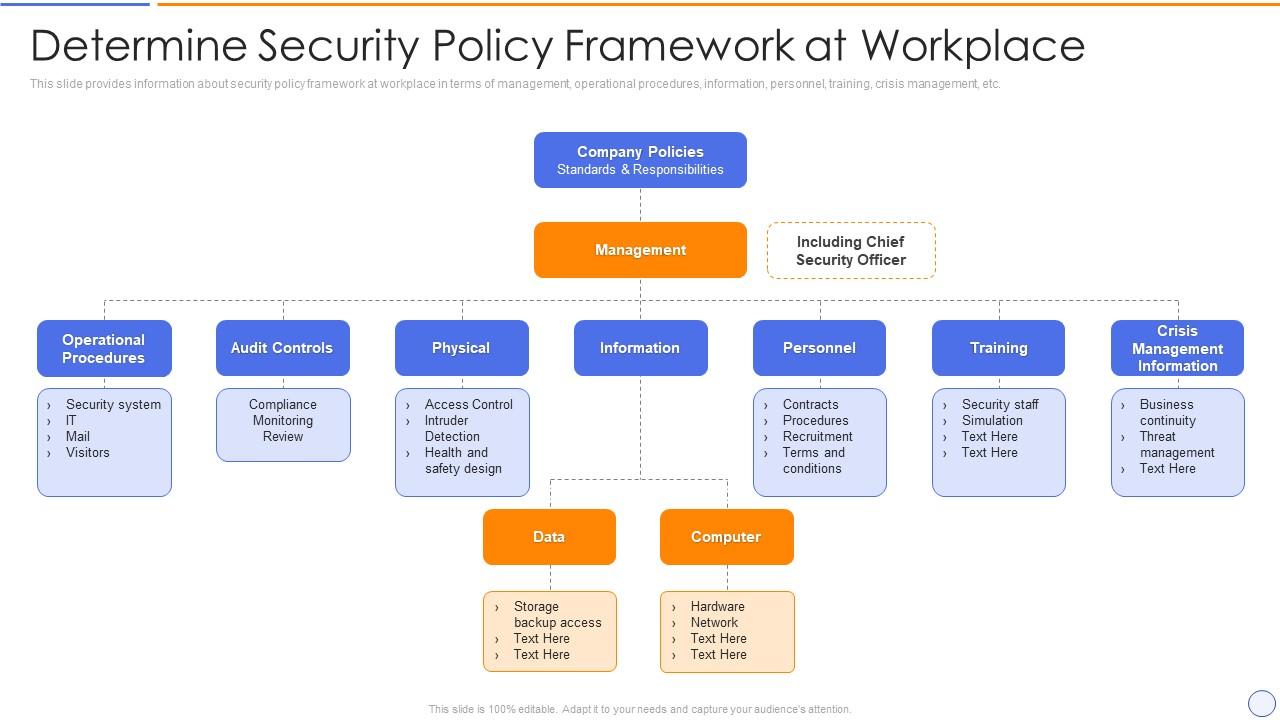


![Access Control Policy [ISO 27001 templates] Access Control Policy [ISO 27001 templates]](https://advisera.com/wp-content/uploads//sites/5/2021/08/A.9.1_Access_Control_Policy_Premium_Preview_EN.png)