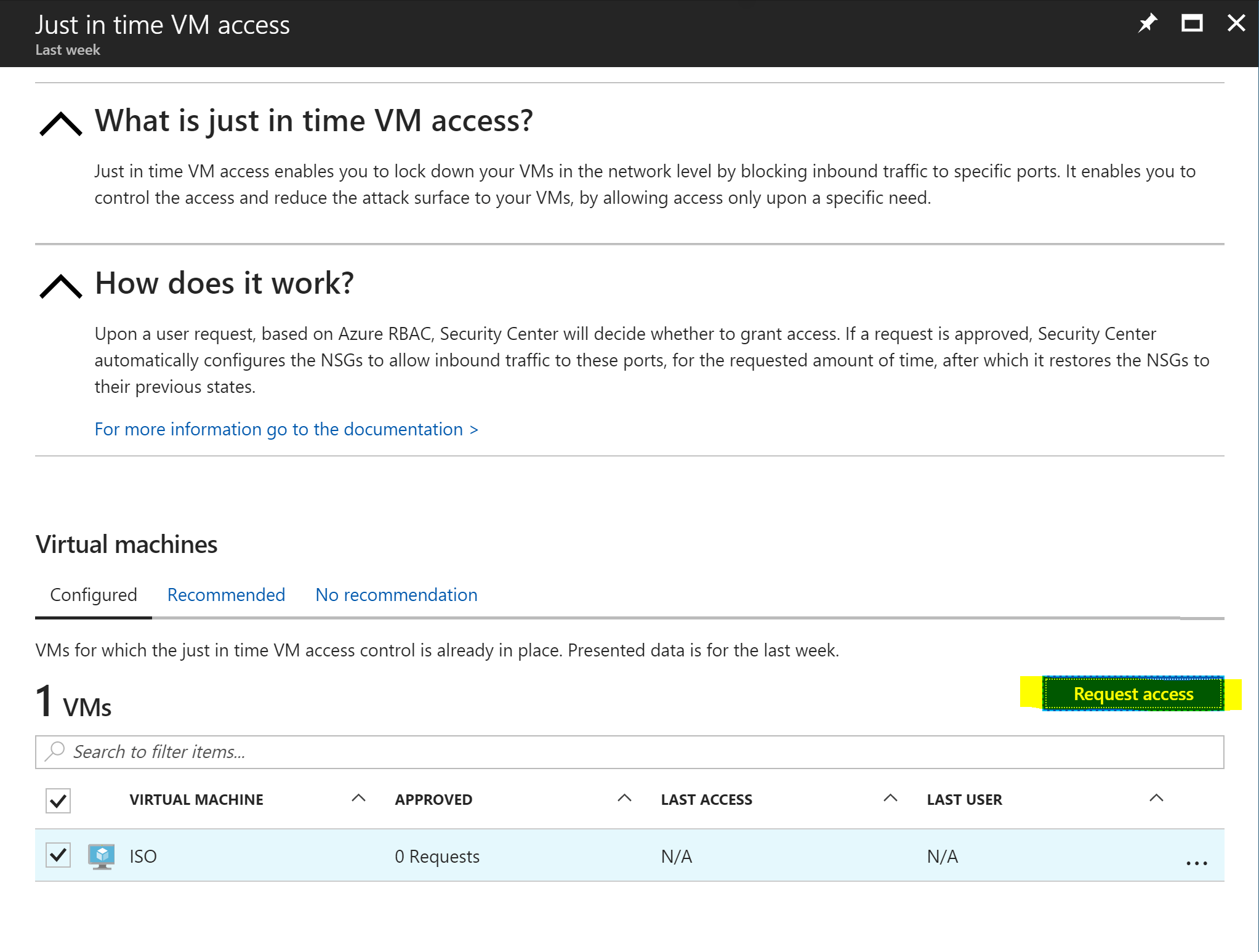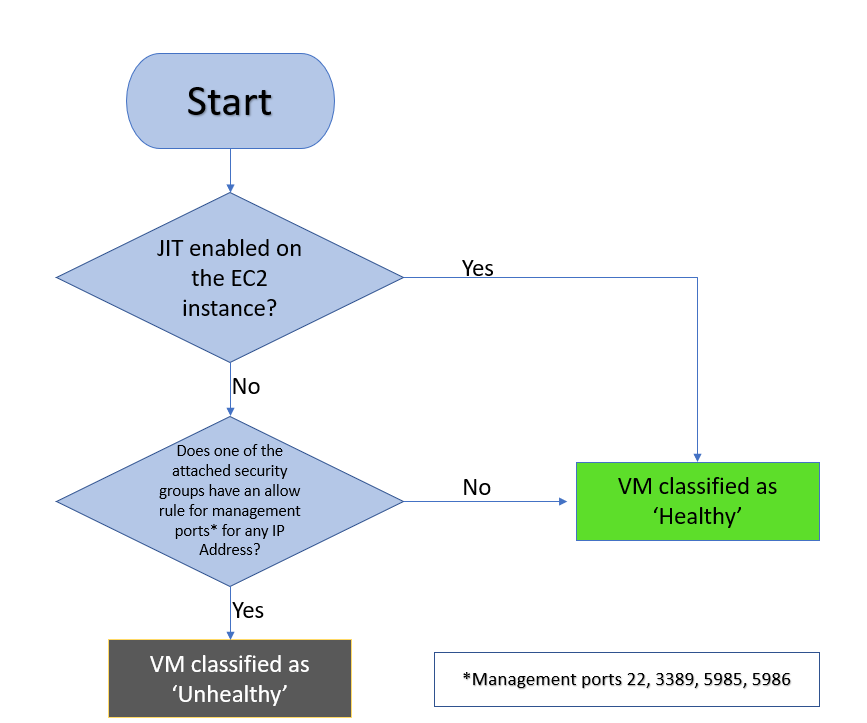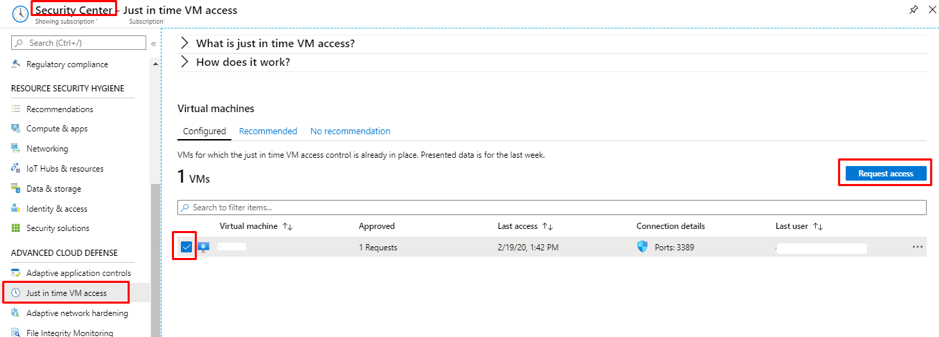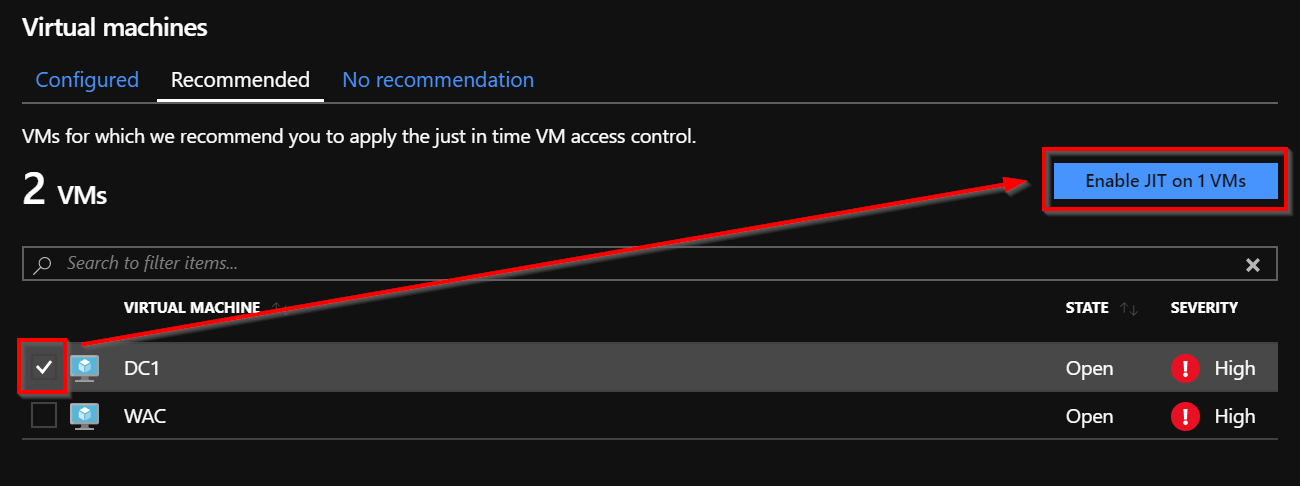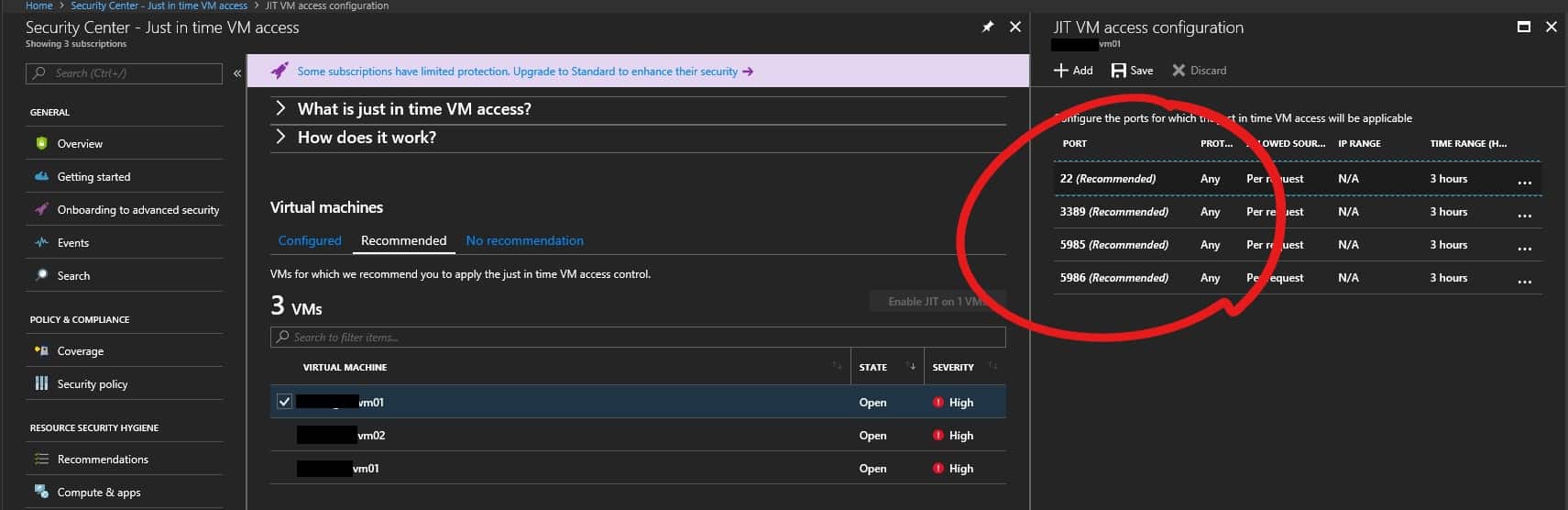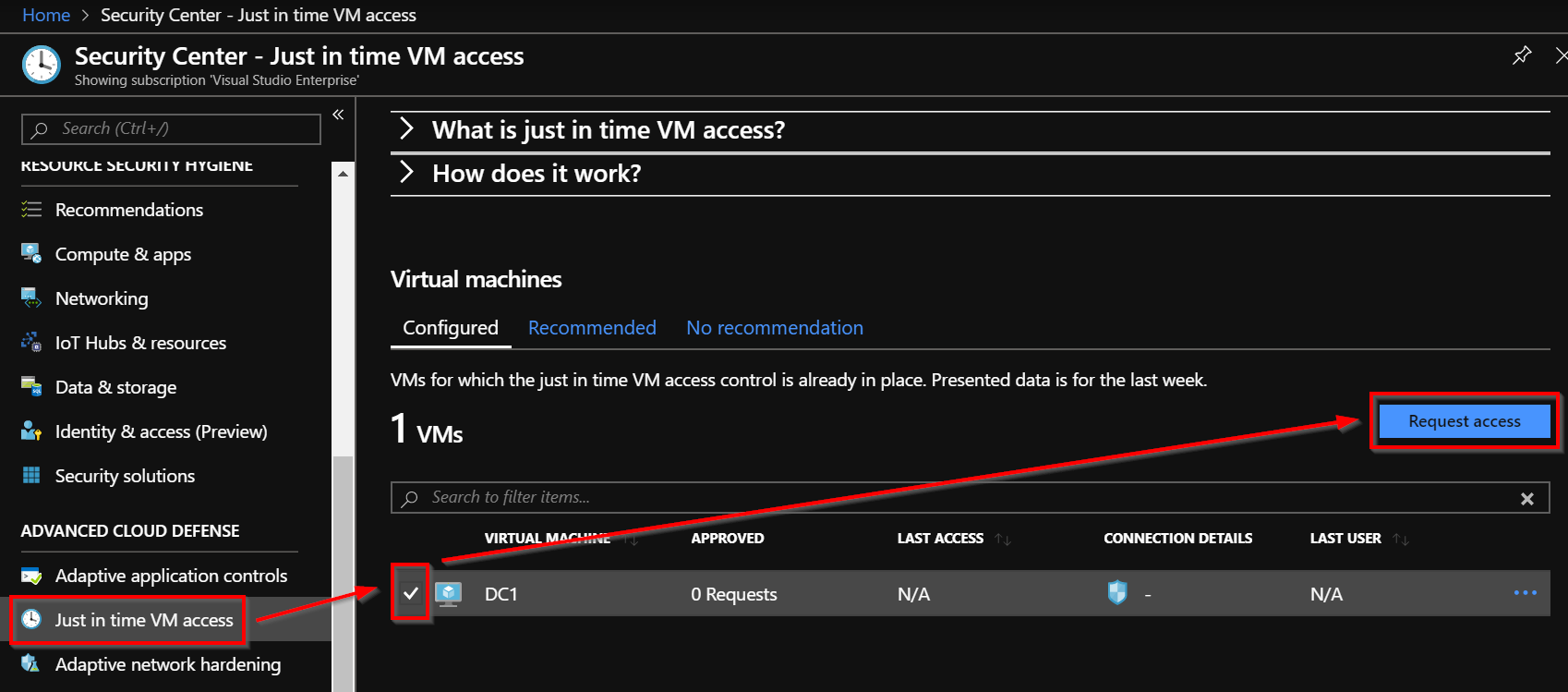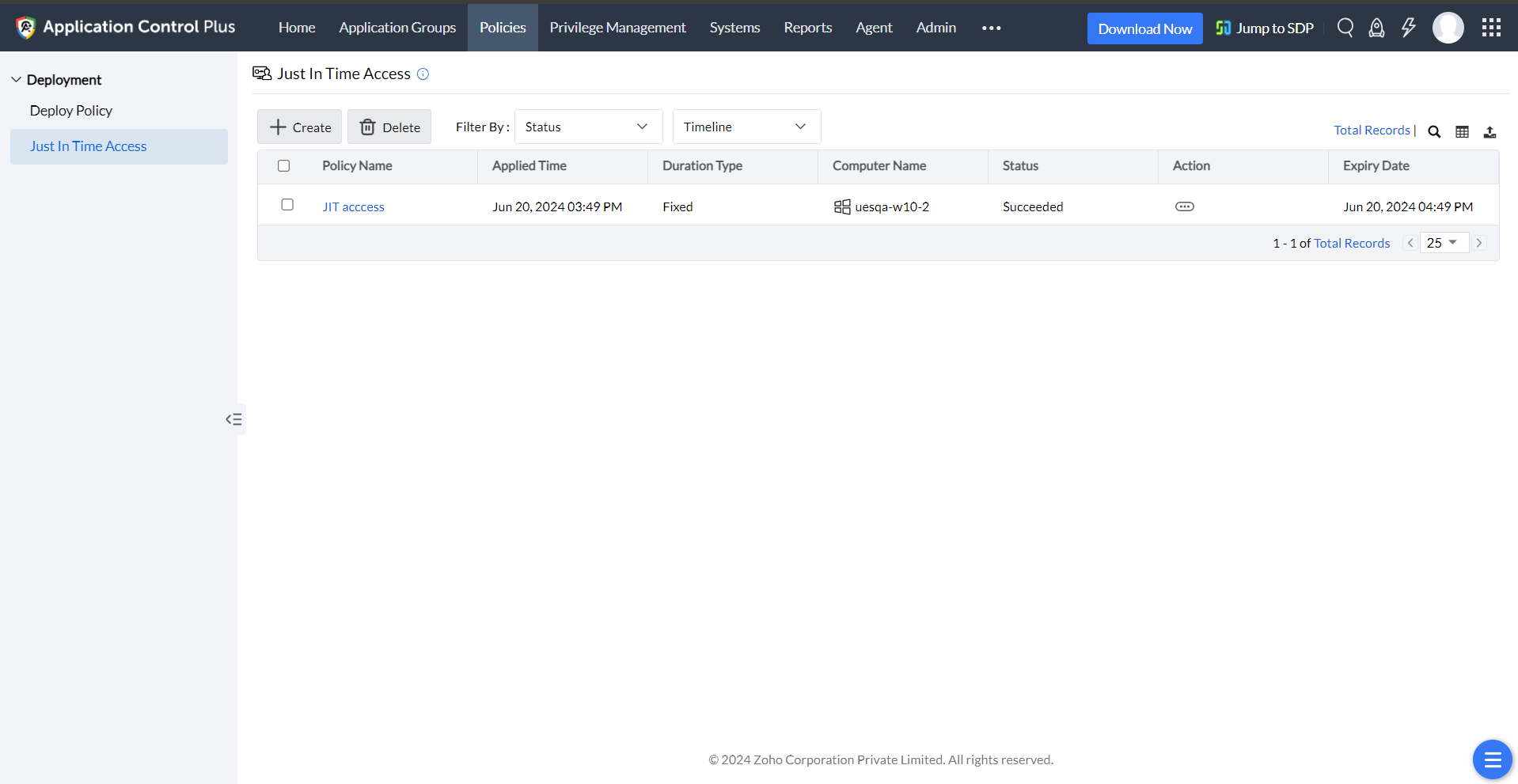
Just In Time Access | How does Just-In-Time (JIT) access work? - ManageEngine Application Control Plus

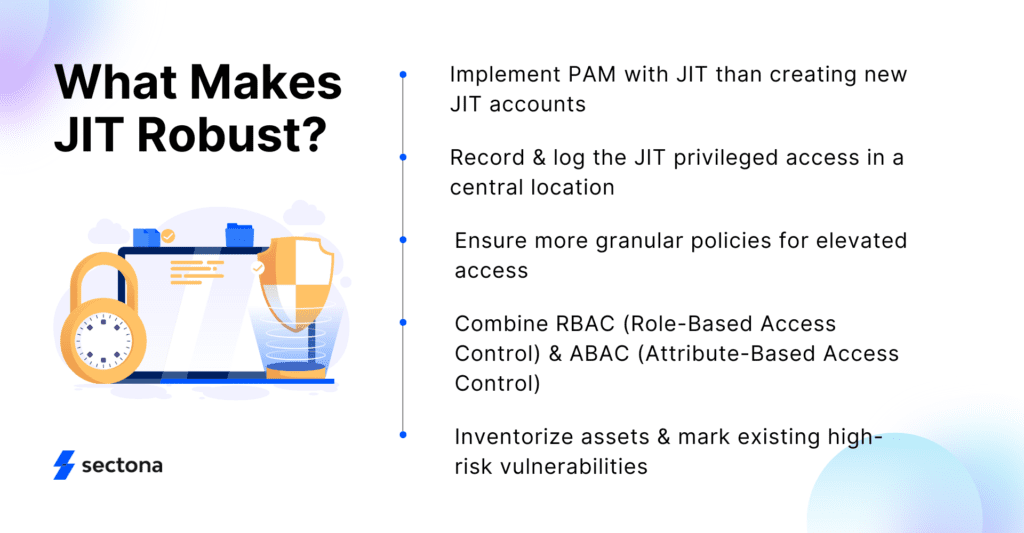
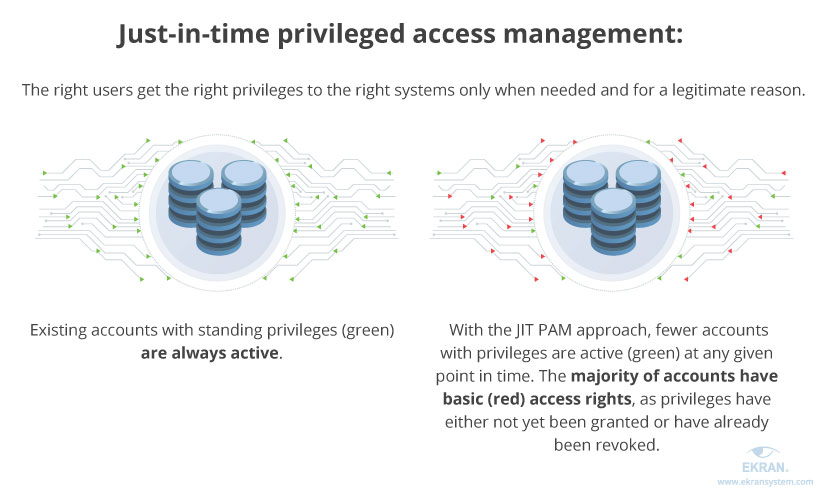
Privileged Identity Management - Just Enough and Just In Time Access Control - Coffee with Conrad - YouTube
Just In Time Access | How does Just-In-Time (JIT) access work? - ManageEngine Application Control Plus
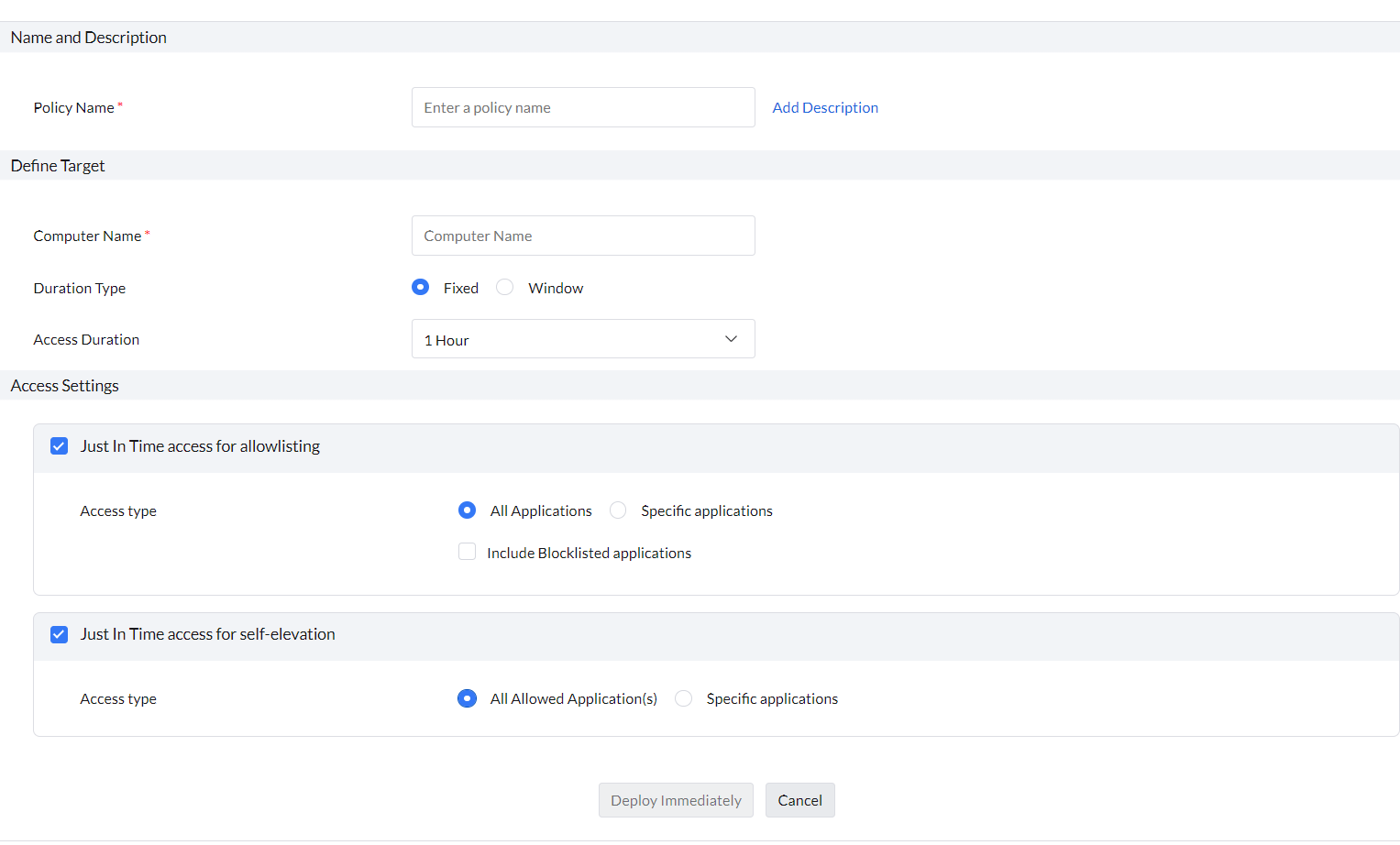
Just In Time Access | How does Just-In-Time (JIT) access work? - ManageEngine Application Control Plus
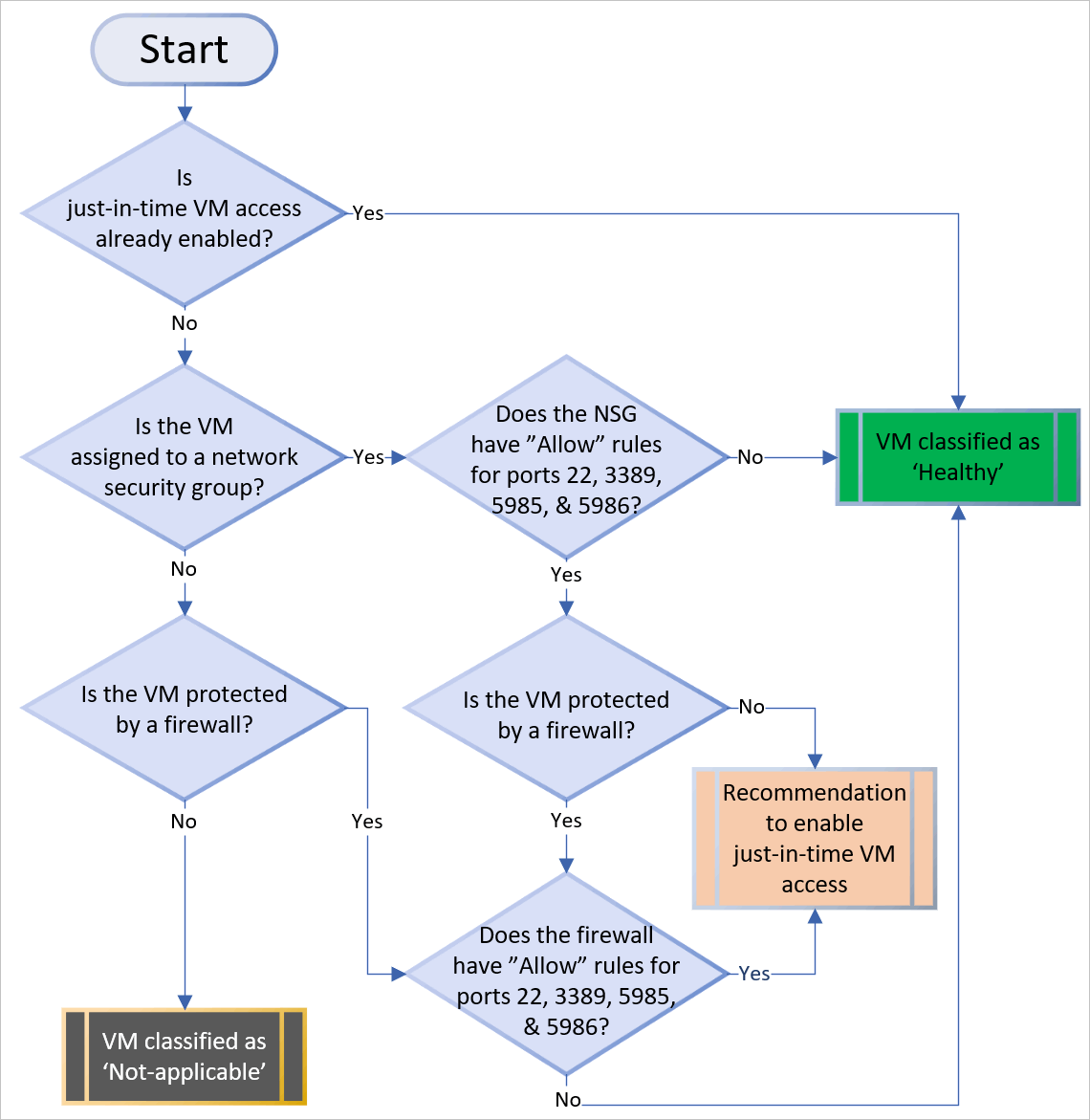
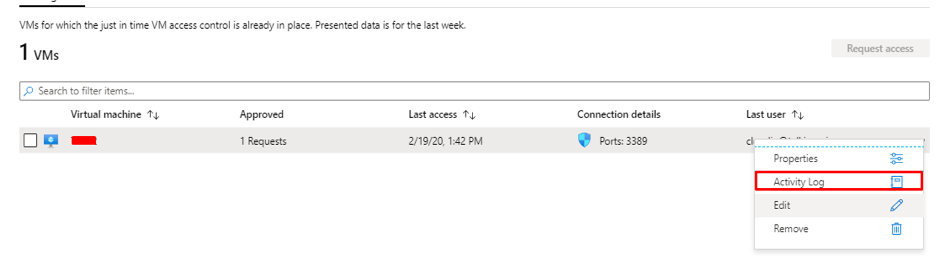
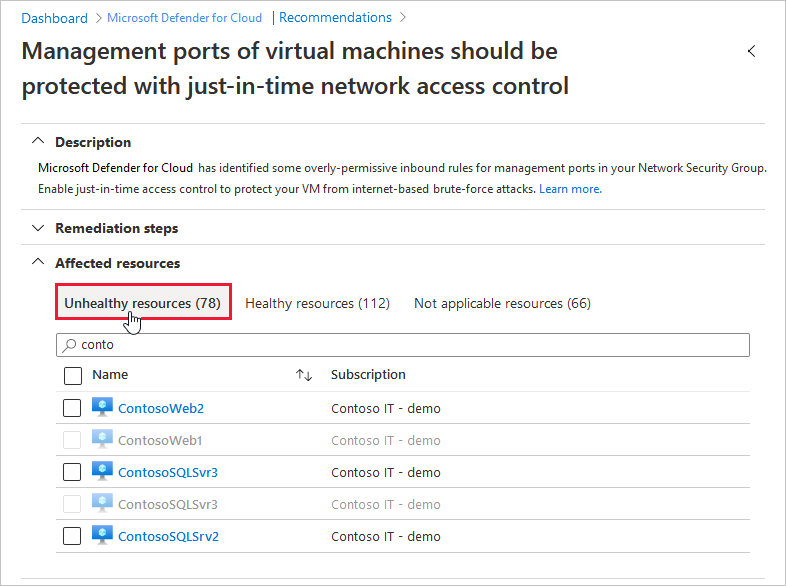
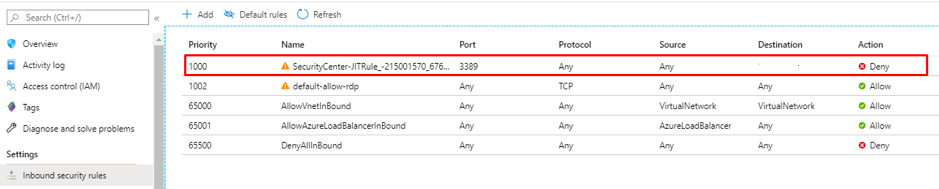
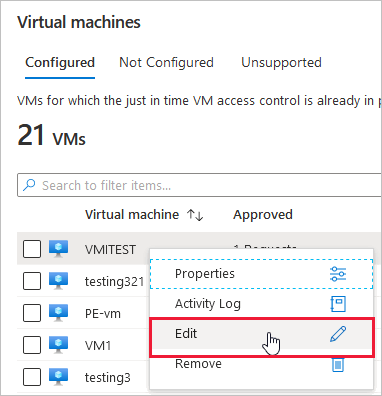
Microsoft Azure – Security Center Just-in-time Deep Dive-Everything related to DevOps and the cloud.